StarKiller - Intro to Empire's Frontend
Note
Make sure to checkout our purposely vulnerable, fully networked, non-standalone Labs to get hands-on experience with Starkiller/Empire or other C2 frameworks.
This’ll be a brief primer post on Starkiller - an Empire C2 front-end. It’ll cover the full process of getting an Agent established with the process of creating a Listener and Stager. Also covered will be running modules for enumeration and persistence along with creating a redirector listener. This post also mimics a youtube video which can be found here https://youtu.be/6H3ymVmFyvA
Listener
Starting off a Listener should be created. The Listener will catch callbacks from beacons i.e. Agents and execute tasks on target machines. Example here an HTTP Listener is chosen.
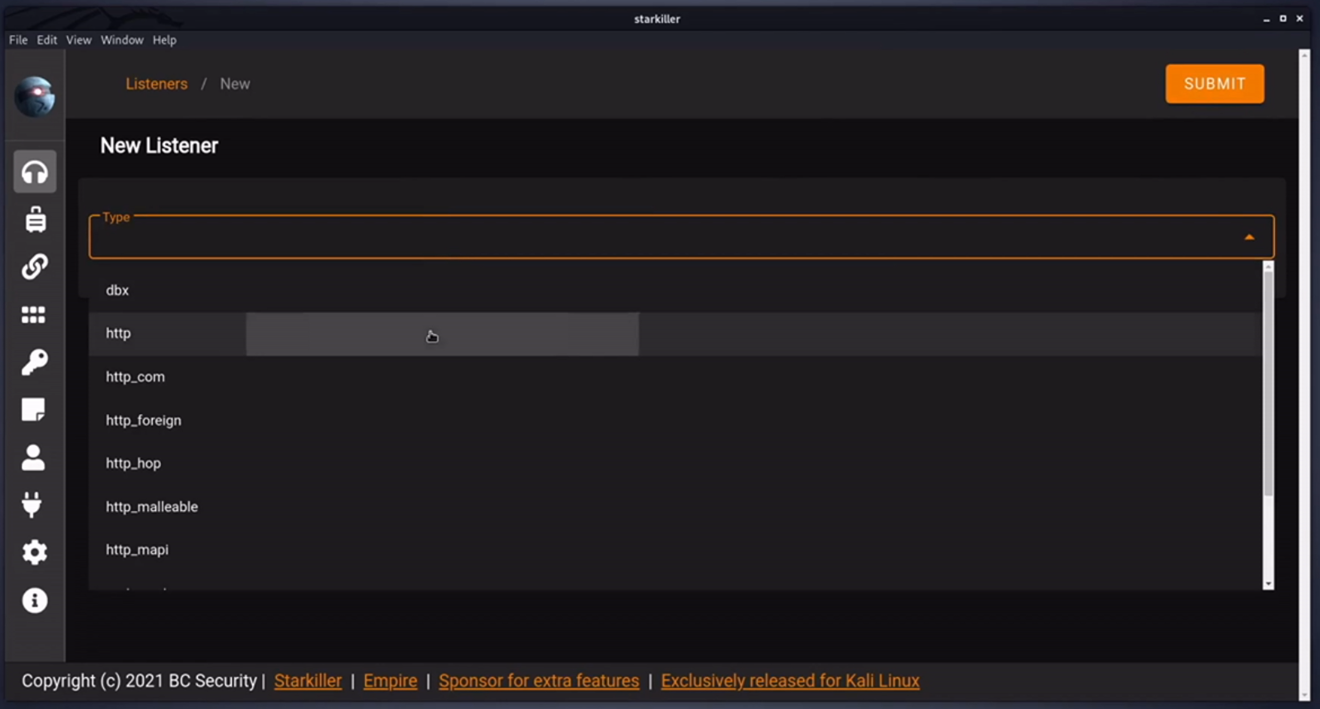
Naming it http-main and setting the listening port to 4448. Also noting any additional settings that can be configured.
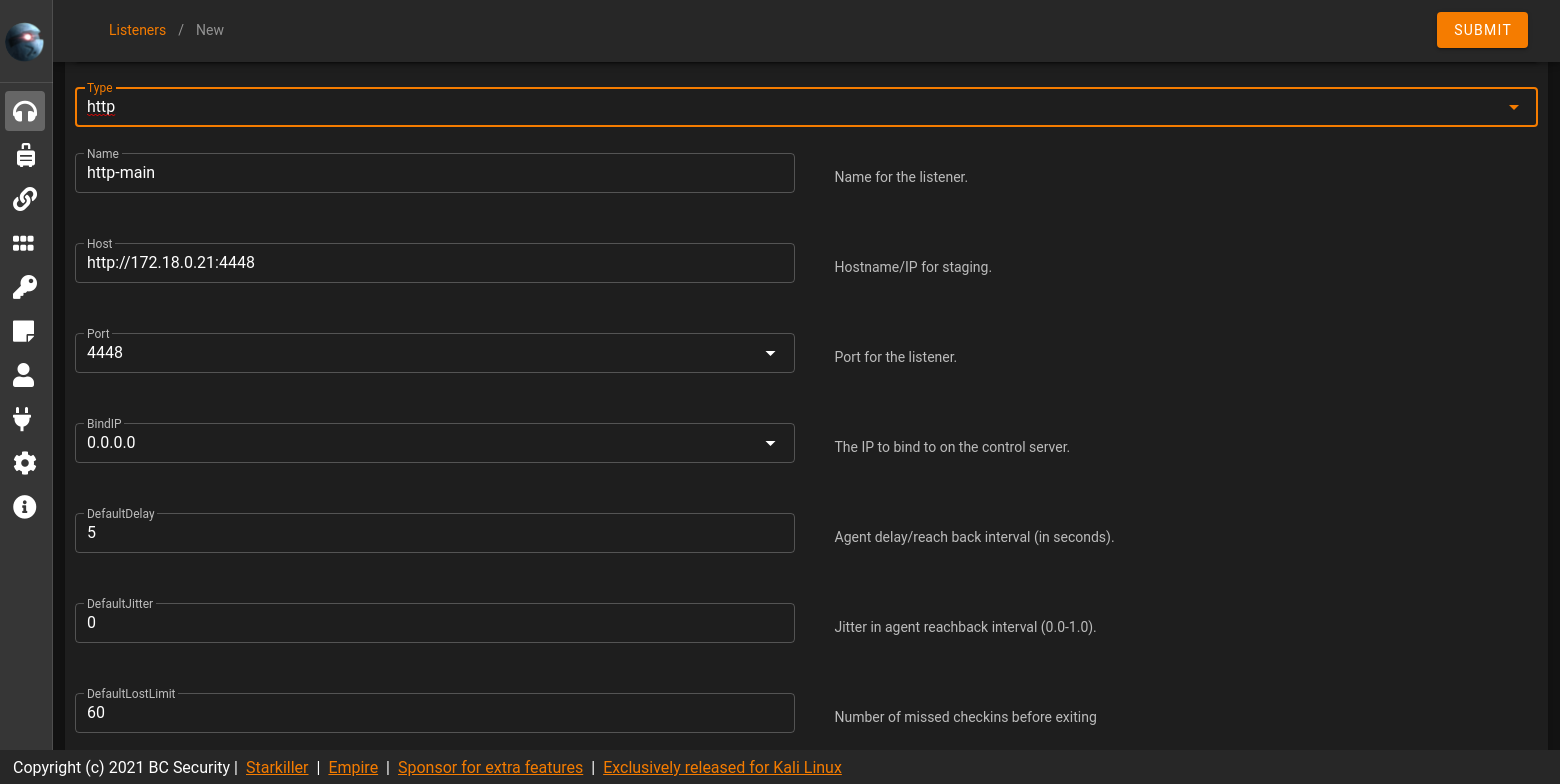
Stager
The next step is to create a payload i.e. Stager that you’ll end up executing (in most cases) on the target to call back to the Listener. Creating a stager is OS dependent and can be exported in a variety formats - from shellcode to a simple script. This example, a Windows batch file is created and set to callback to the newly created Listener of http-main.
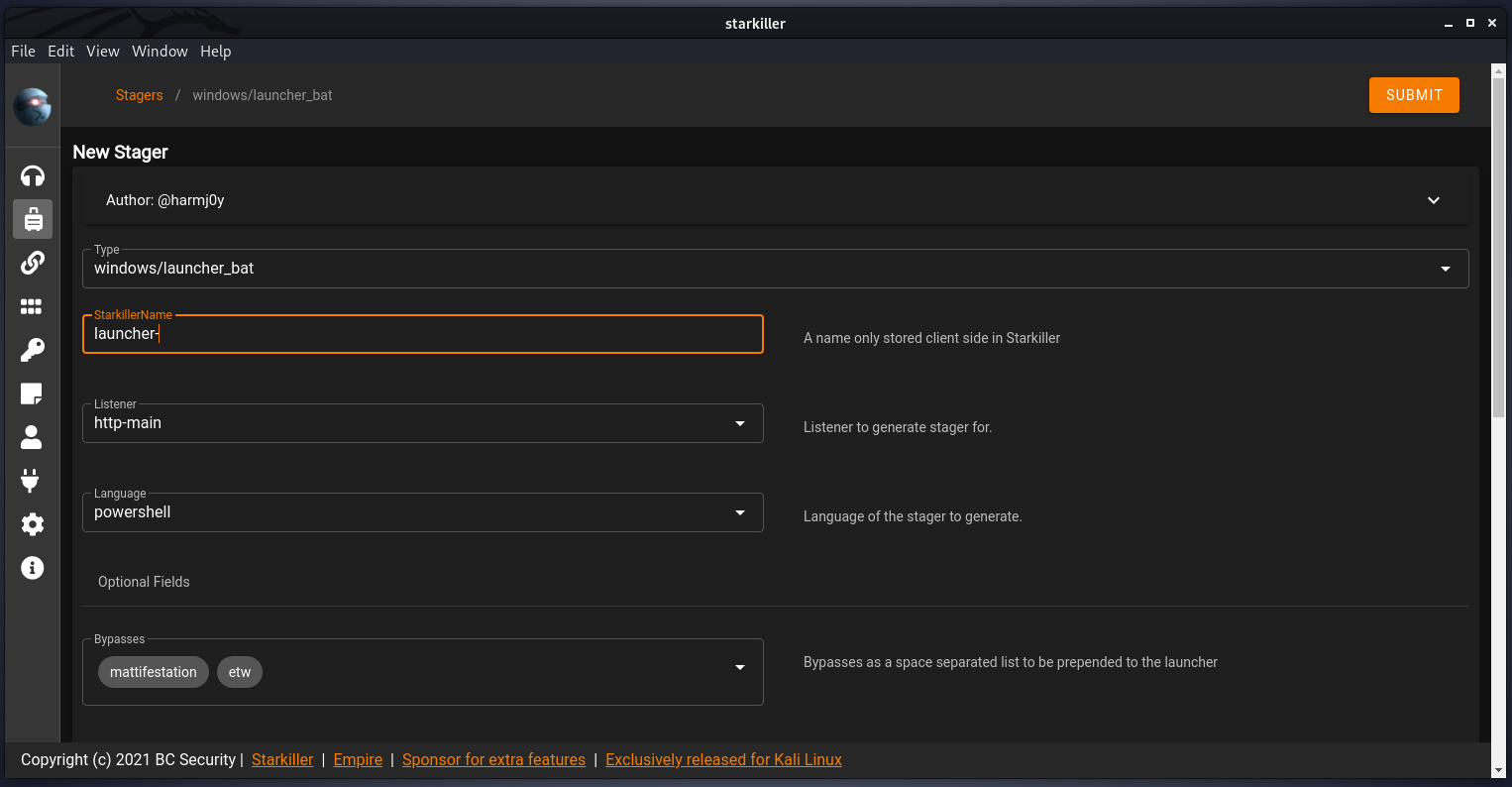
Agent
Once the stager is exported, it’ll need to be executed on that target. Once executed without any AV hiccups you should receive a callback with a newly established Agent.
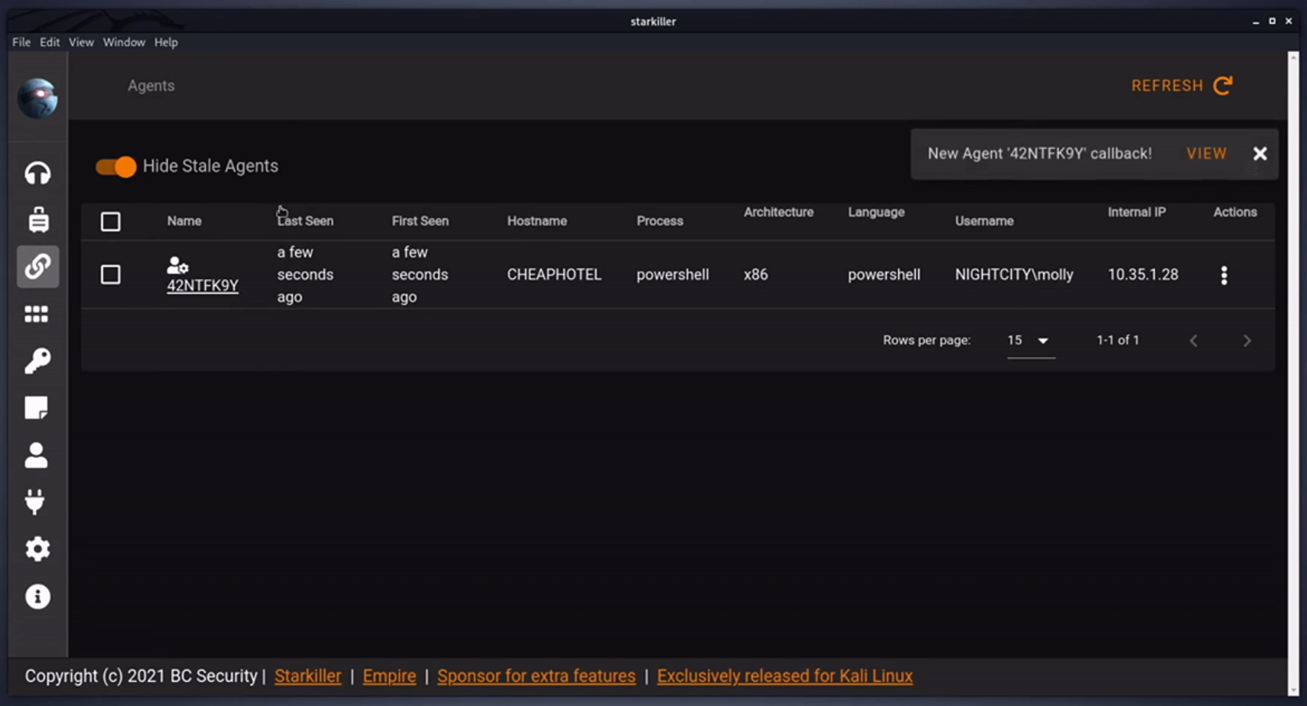
Next you can task your agent to execute modules. This can be done in the Agent itself or in the Modules tab, shown below.
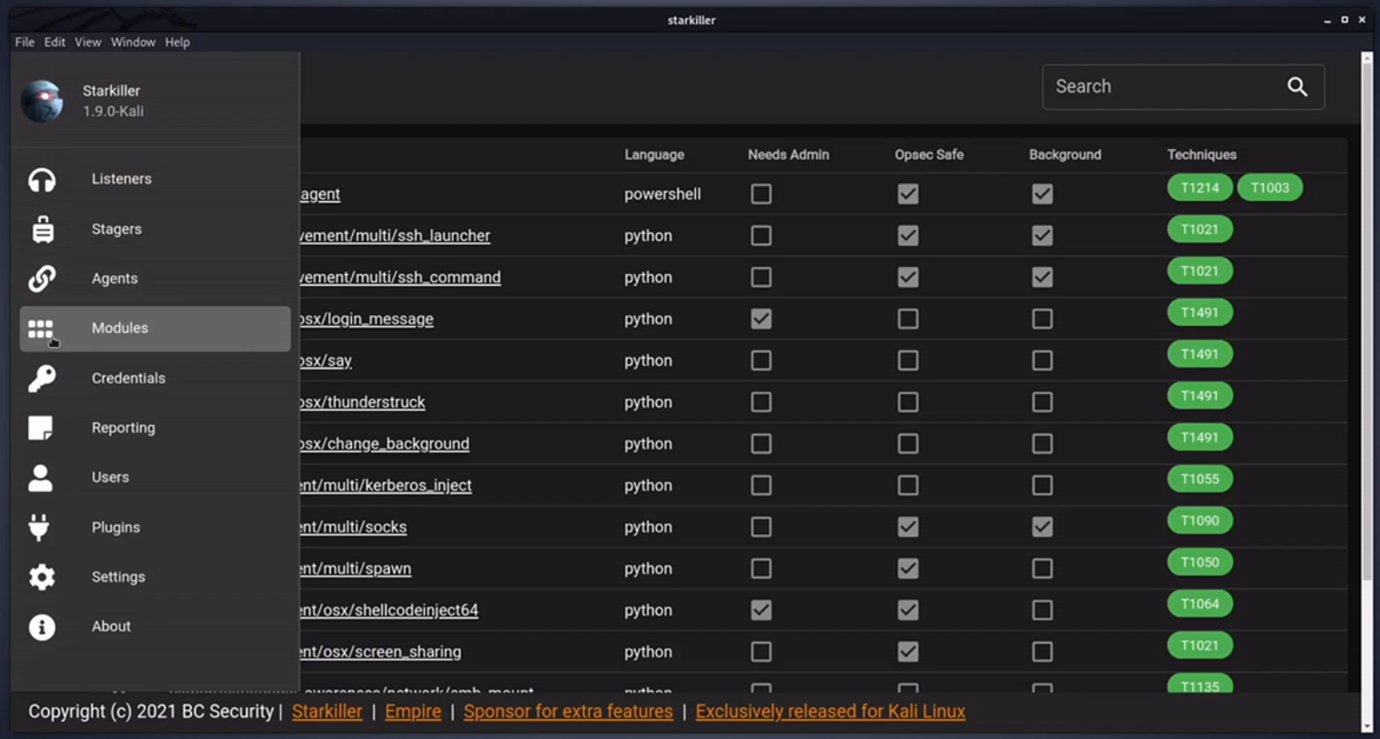
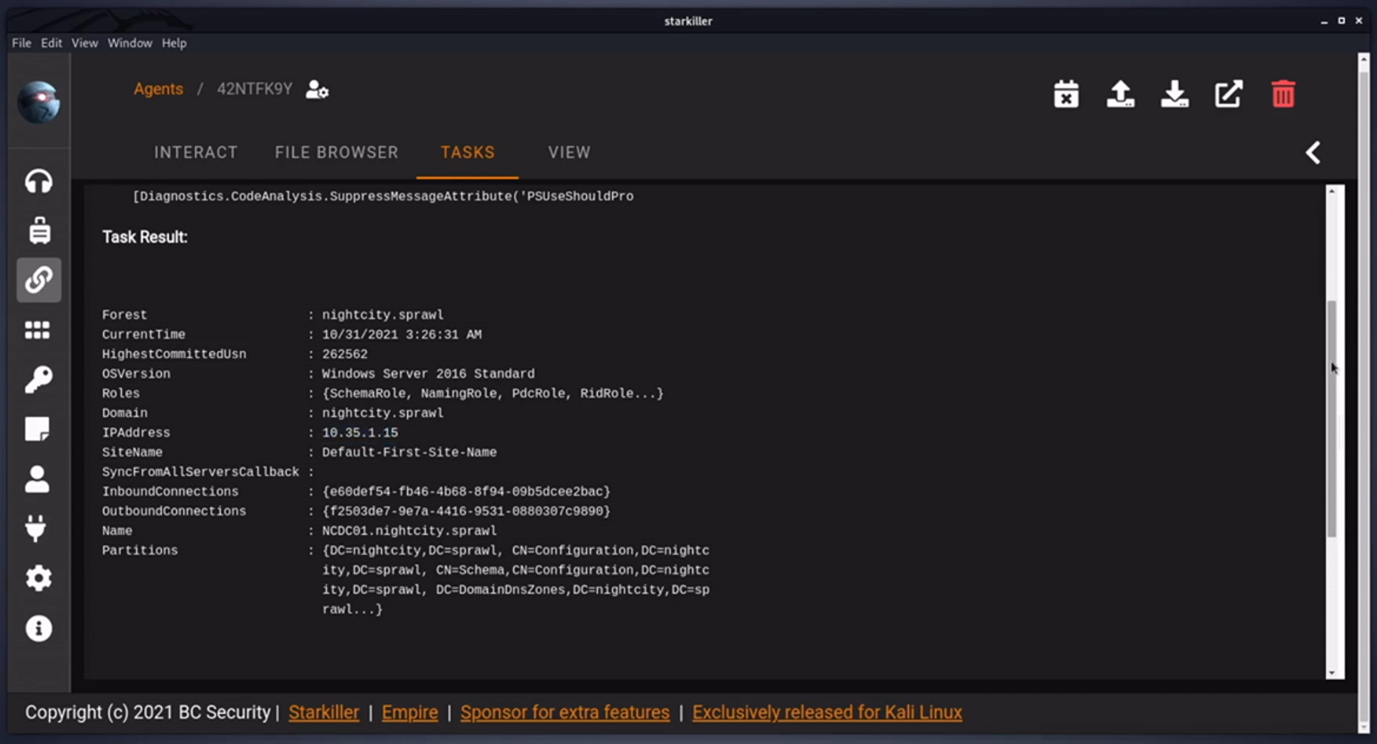
Here we’ll roll with an AD enumeration module in PowerView. This will get basic info about the Domain Controller in our targets Domain.
Persistence
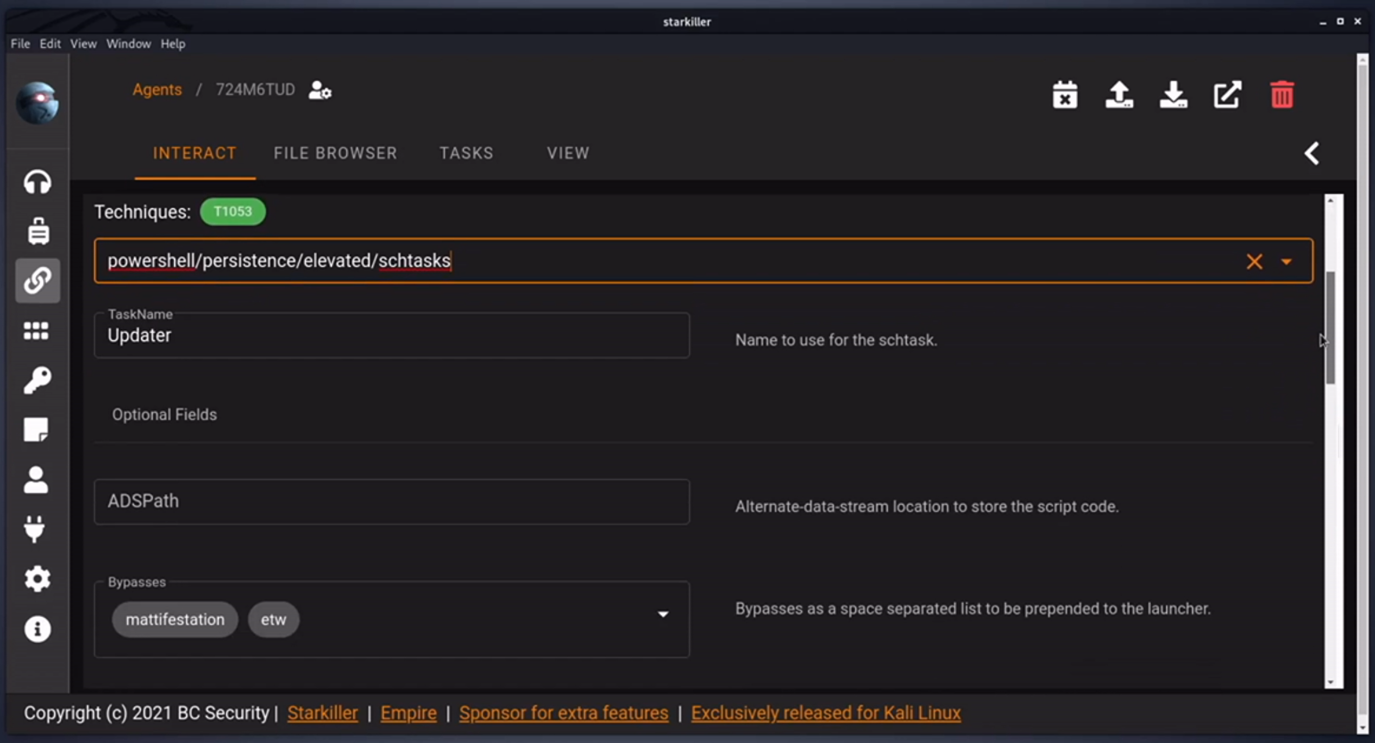
Many persistence modules also exist, one of which is setting a Windows scheduled task. This will callback to our listener within a specific time interval which is completely customizable.
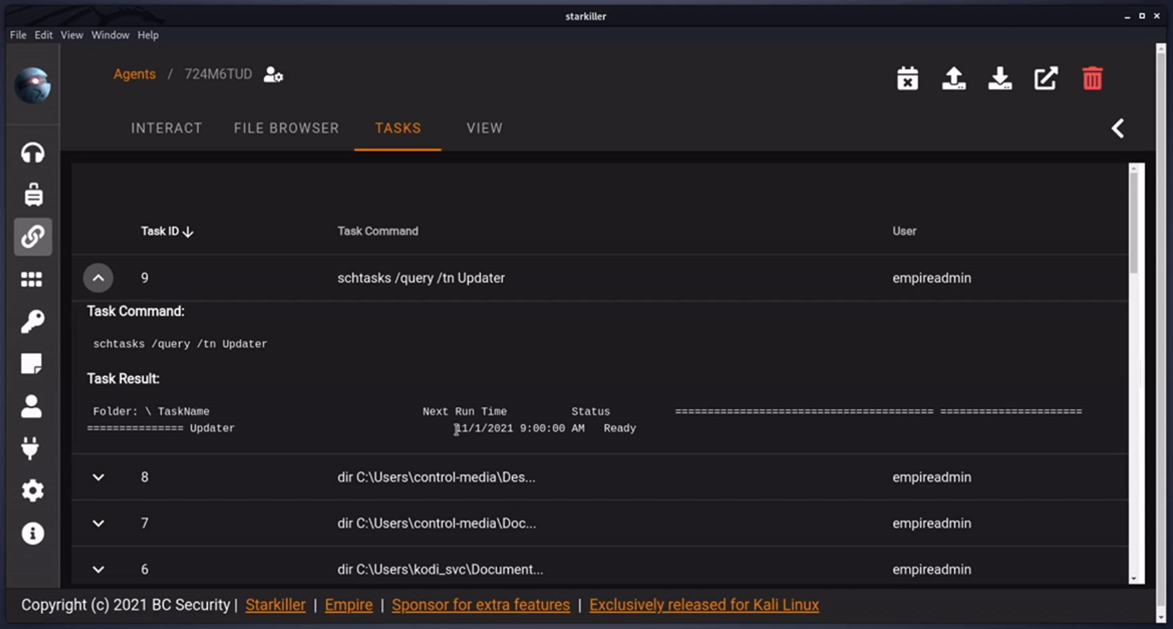
Once this scheduled task is set, you can check manually by running a direct Shell Command in the Interact tab eg schtasks /query /tn Updater. Which produced the results below.
Redirector Listener
The are a variety of listener options as well. One that may be useful is the Redirector Listener. This will forward traffic from one Agent to another Agent then back to Empire, like a proxy. This is useful to gain access to internal networks, alter traffic to blend in or bypass any security mechanisms that may limit further network access.
The following are a few notes on setting up a Redirector on Starkiller
-
Name: The exact name of the existing Agent where you’d like to create the redirector. This will eventually task that Agent to open and listen on a port for redirection.
-
Listener: An existing Listener on Empire (or another redirector) which your new Redirector will forward to.
-
ListenPort: The new redirection port which will listen on an existing Agent.
-
InternalIP: What IP the Redirector will listen on - multi-homed targets for network pivoting.
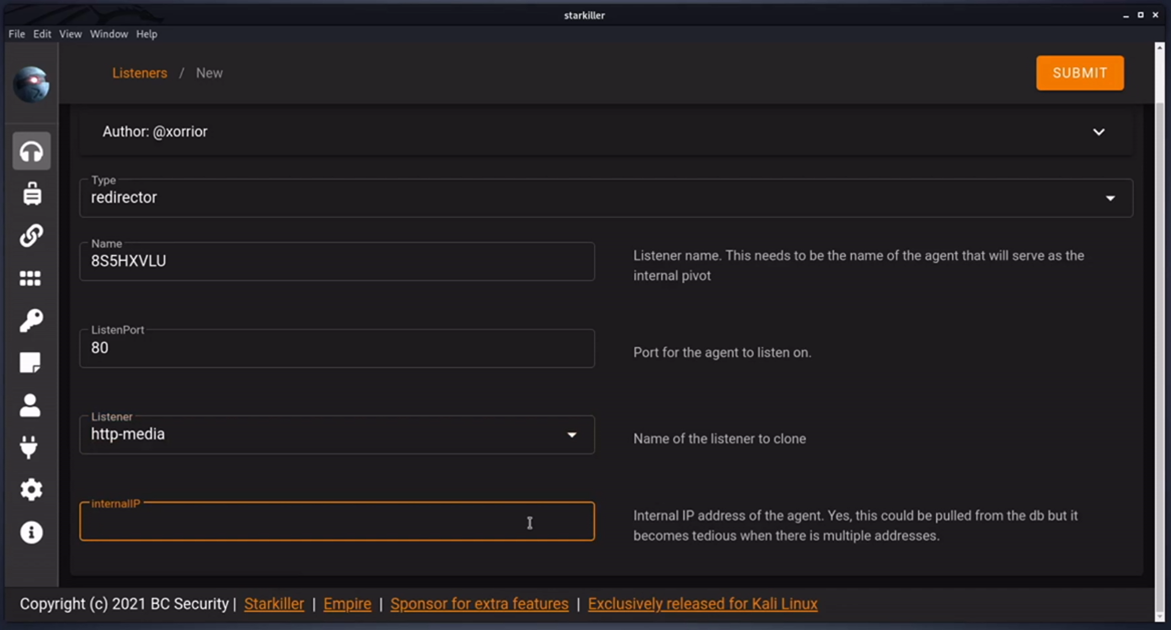
Once complete, the Agent will be tasked to create the redirector. Then, when you create a new Stager you’ll have the option to use this redirector as a Listener.
Checkout the Starkiller repo on github along with BC-Security’s official intro to Starkiller for updates and further info.